Blue Eagle orchestrates alliances with venerated Partners and Vendors, enhancing our mastery in furnishing holistic Cyber Security Solutions. From robust bastions to orchestrated threat dance, our collaborations deliver avant-garde defenses personalized for your digital sovereignty.
Endpoints Protection
Embark on a journey of fortified cybersecurity with Endpoint Sentinel, an exclusive offering from Blue Eagle Precision. Crafted to shield laptops, desktops, mobile devices, and servers from the lurking threats of the digital realm, this avant-garde solution encompasses antivirus, anti-malware, anti-spyware software, firewalls, and intrusion prevention systems.
The advantages of embracing the Endpoint Sentinel service by Blue Eagle Precision encompass:

- Elevated Security: Endpoint Sentinel by Blue Eagle Precision is the ultimate bulwark against malware, viruses, and malevolent software. Its real-time protection ensures a strong defense, significantly minimizing the risk of data breaches and security incidents.
- Enhanced Surveillance: The Endpoint Sentinel service provides a glimpse into the world of endpoint activities, empowering organizations to closely monitor and track endpoints. This early detection of cyber threats amplifies incident response capabilities and accelerates the resolution process.
- Centralized Governance: The Endpoint Sentinel service offered by Blue Eagle Precision introduces a centralized hub for management and reporting, streamlining the task of maintaining endpoint security across the organization. This operational efficiency enhancement is of utmost significance.
- Alignment with Regulations: The Endpoint Sentinel service aids organizations in meeting regulatory compliance prerequisites. It equips them with security controls harmonized with industry and government regulations.
- Economical Assurance: Endpoint Sentinel from Blue Eagle Precision extends beyond bolstering security. It paves the way for cost savings by curbing the risk of security incidents, optimizing incident response procedures, and simplifying management and reporting.
Perimeter Protection
At Blue Eagle Precision, the realm of cybersecurity extends to the edge with Perimeter Sentry. This avant-garde offering fortifies an organization's network by erecting a protective barrier between its internal infrastructure and the vast digital wilderness beyond, which includes the internet.
The implementation of Perimeter Sentry encompasses the deployment of impregnable firewalls, vigilant intrusion prevention systems, fortified virtual private networks (VPNs), and an arsenal of other cutting-edge security technologies. These measures collectively thwart unauthorized access and safeguard the network from the relentless onslaught of cyber threats.
The advantages bestowed by the adoption of Perimeter Sentry are as follows:
- Elevated Protection: Perimeter Sentry acts as an unwavering guardian, staunchly preventing cyber threats from infiltrating the organization's network by establishing an impervious barrier between its internal and external realms. This proactive stance significantly diminishes the vulnerability to data breaches and other malicious incidents.
- Augmented Insight: The vigilance of Perimeter Sentry extends to providing a comprehensive overview of network activities, empowering organizations to meticulously monitor and trace network traffic for the early detection and thwarting of cyber threats. This heightened situational awareness accelerates incident response and minimizes the time taken to detect and rectify security breaches.
- Centralized Governance: The mastery of Perimeter Sentry, meticulously cultivated by Blue Eagle Precision, introduces an integrated hub for the orchestration and reporting of network security. This consolidation of management tasks significantly streamlines the upkeep of network security across the organization, enhancing overall operational efficiency.
- Conformity with Regulations: Perimeter Sentry equips organizations with an invaluable tool to meet regulatory compliance mandates. By furnishing robust security controls that harmonize with industry and government regulations, it serves as a cornerstone for upholding legal and industry standards.
- Economical Assurance: Perimeter Sentry, the embodiment of cybersecurity vigilance, not only bolsters security but also paves the way for fiscal prudence. By mitigating the risks associated with security breaches, optimizing incident response, and simplifying management and reporting processes, it translates into substantial cost savings.
In essence, the Perimeter Sentry service, an embodiment of Blue Eagle Precision's commitment to cybersecurity, bestows organizations with an enhanced shield of security, amplified awareness, streamlined governance, regulatory adherence, and a path to financial resilience.
Privilege Access Management Unveiled
Diving into the realm of fortified cybersecurity, Blue Eagle Precision presents a solution that redefines access control - Privilege Access Management (PAM). This cutting-edge security strategy is meticulously designed to equip organizations with the ultimate authority to govern access to their critical systems and sensitive information within their IT framework. PAM takes the role of a vigilant guardian, overseeing privileged accounts, which hold escalated access privileges beyond standard user credentials.
The integration of PAM brings forth an array of transformative advantages:
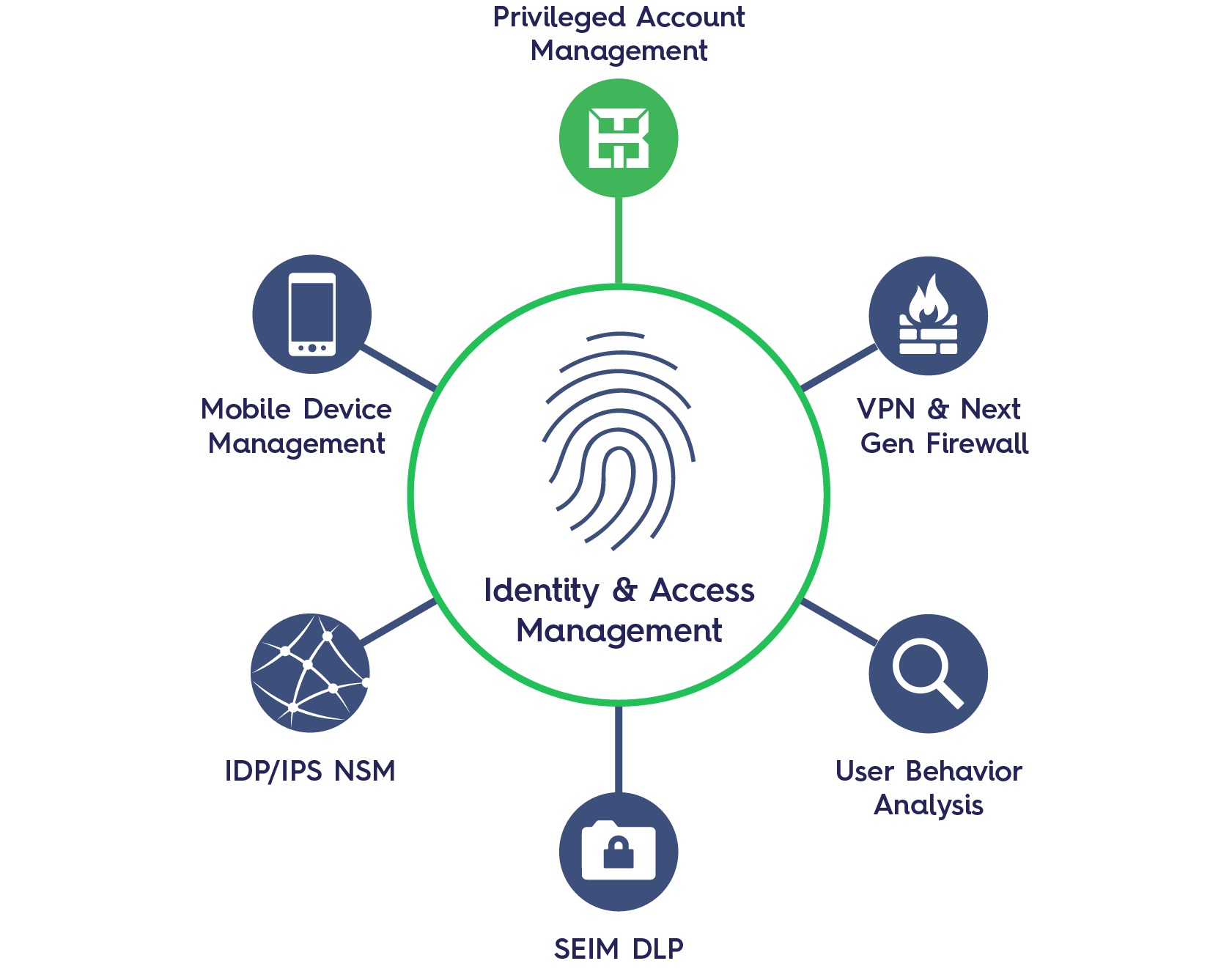
- Elevated Security Control: PAM grants organizations the power to orchestrate access to crucial systems and sensitive data with precision. This proactive measure significantly curbs the risk of unauthorized entry, data breaches, and various security vulnerabilities.
- Adherence to Regulatory Mandates: PAM stands as a steadfast compliance companion, enabling organizations to seamlessly adhere to intricate regulatory standards. Its centralized command over privileged access, audit trail generation, and policy enforcement align perfectly with industry and government regulations.
- Boosted Operational Efficiency: PAM's automation extends to pivotal processes like password management, access request workflows, and approval procedures. By streamlining these processes, PAM eases the workload on IT personnel, thereby enhancing the operational efficiency of the entire organization.
- Enhanced Accountability Mechanism: PAM's watchful eye introduces unprecedented transparency into system interactions. Not only does this enable the identification of users accessing specific resources, but it also bolsters accountability for actions taken and simplifies the investigation of potential security incidents.
- Optimized Resource Allocation: Beyond security benefits, PAM also extends its impact to fiscal prudence. By simplifying access management processes and minimizing the need for manual interventions, PAM contributes to a noticeable reduction in operational costs.
Software-Defined Wide Area Networking (SD-WAN)
Experience the future of networking with Software-Defined Wide Area Networking (SD-WAN) by Blue Eagle Precision. Seamlessly connect branch offices, data centers, and cloud resources across expansive wide area networks (WANs) using software-defined networking (SDN) principles.
SD-WAN solutions revolutionize network architecture, replacing traditional WAN technologies like Multiprotocol Label Switching (MPLS) with a virtual overlay network. Software intelligently manages and optimizes network traffic across various links, including high-speed broadband, wireless, and private circuits.
Benefits of Blue Eagle Precision's SD-WAN solutions:
- Enhanced Performance: Optimize network traffic, resulting in improved application performance and user experience.
- Increased Security: Utilize advanced security measures to protect against cyber threats, reducing data breach risk.
- Simplified Management: Centrally manage and report network security, enhancing overall efficiency.
- Cost Savings: Reduce costs by optimizing network traffic and eliminating reliance on expensive circuits.
- Scalability: Easily adapt to changing needs, adding new branches and resources seamlessly.
Security Operations Center (SOC)
Our SOC as a Service offers a comprehensive solution for managing security operations center functions. Powered by cutting-edge technologies, threat intelligence, and skilled human expertise, we provide continuous monitoring and responsive actions to security incidents.
Advantages of embracing SOC as a Service:
- Real-time Threat Detection and Response: Our SOC as a Service harnesses advanced technologies and threat intelligence to swiftly identify and counteract security incidents, curtailing the risk of data breaches and cyber threats.
- Expert Security Professionals: A seasoned team of security analysts and engineers, well-versed in identifying and managing security incidents, collaborates with organizations to heighten security posture and relieve internal IT staff.
- Proactive Security Vigilance: Our SOC as a Service offers 24/7 monitoring of networks and endpoints, furnishing immediate alerts about potential security breaches. This empowers organizations to preclude threats before they materialize.
- Economical Security Solution: Blue Eagle's SOC as a Service presents a cost-effective alternative to establishing and sustaining an in-house security operations center. Avail advanced security capabilities without hefty investments.
- Regulatory Compliance: Abide by industry and governmental security monitoring and incident response regulations, such as GDPR and HIPAA, with assistance from our SOC as a Service.
- Enhanced Incident Response: Augment your incident response capabilities with our SOC as a Service, offering real-time alerts, notifications, incident response strategies, and support.

CyberSOC Africa operates an in-country, ISO certified security operations center (iSOC) empowered by cutting-edge technology and a team of elite cyber experts. With a focus on design, quality, engineering, and best-in-breed technologies, we ensure comprehensive cyber enforcement and technological prowess. Our SOC as a Service, tailored to your unique requirements, delivers unparalleled cyber expertise and resilience.
Data Loss Prevention System (DLP)
Data Loss Prevention (DLP) solution we provide is meticulously designed to thwart unauthorized data disclosure, alteration, or destruction. Our DLP solutions, available as software agents or appliances, vigilantly monitor and control data movements within your network, endpoints, and cloud services.
Advantages of embracing our state-of-the-art DLP system:
- Safeguard Sensitive Data: Shield sensitive data like PII, intellectual property, financial records, and confidential business information from unauthorized access, loss, or theft.
- Regulatory Compliance: Align with data protection regulations like GDPR and HIPAA, ensuring adherence to industry and government standards.
- Enhanced Security: Deploy advanced security features including data encryption, masking, and classification, mitigating data breach risks and fortifying incident response.
- Unveil Data Flows: Gain visibility into data movement across networks, endpoints, and cloud services, empowering real-time monitoring, usage tracking, and threat detection.
- Streamlined Management: Our DLP solutions offer centralized management and reporting, lightening the load on IT staff for enhanced operational efficiency.
- Economical Data Security: Trim expenses by reducing data breach risks, avoiding regulatory penalties, and improving incident response readiness.







